Enlarge (credit: Getty Images) Distributed denial-of-service attackers have seized on a new vector for amplifying the junk traffic they lob at targets to take them offline: end users or networks using the Plex Media Server. DDoS amplification is a technique that leverages the resources of an intermediary to increase the firepower of attacks. Rather than […]
Tag: Tech
Zoombombing countermeasures are ineffective in the vast majority of cases
Enlarge As the COVID-19 pandemic forced schools, colleges, and businesses to limit in-person meetings, the world quickly adopted video conferencing from services such as Zoom and Google Meet. That, in turn, gave way to “zoombombing,” the term for when Internet trolls join online meetings with the goal of disrupting them and harassing their participants. Meeting […]
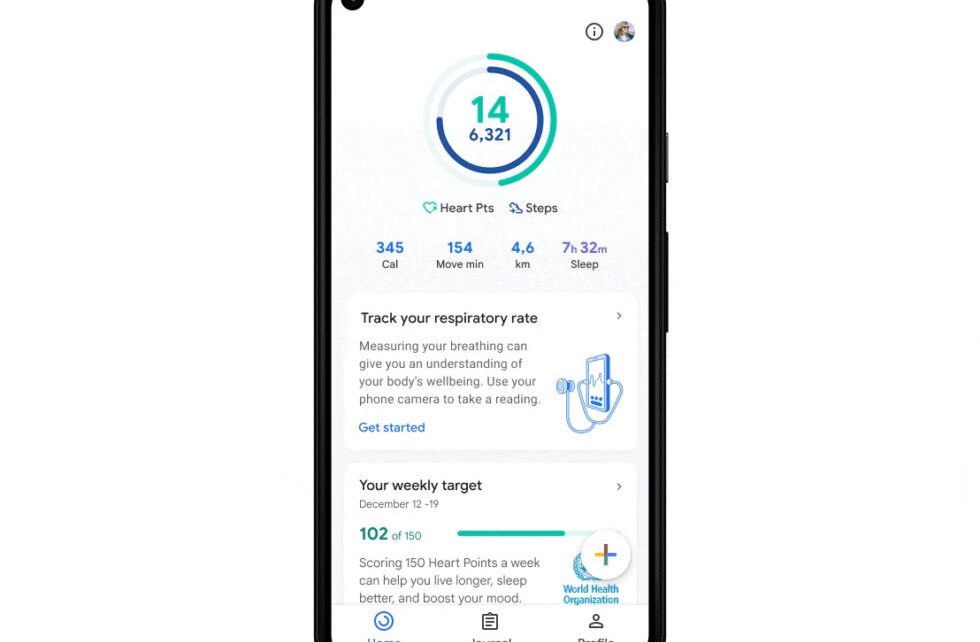
Google Pixel phones will soon track heart rate using only the camera
Google Fit for Pixel phones will have this new card in the middle for vitals tracking. [credit: Google ] Google’s latest Pixel-exclusive feature is the ability to track your heart rate and respiratory rate, without any extra hardware. The company says that, starting next month, Google Fit on Pixel phones will track these health stats using […]
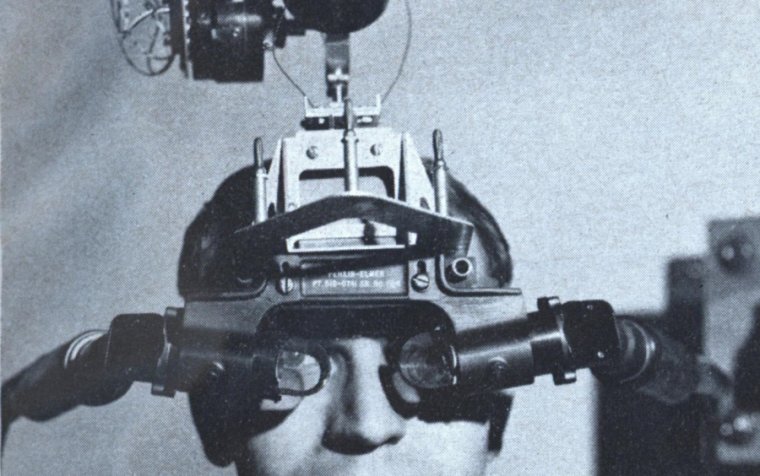
New report on Apple’s VR headset: 8K in each eye, potential $3,000 price tag
Enlarge / The “Sword of Damocles” head-mounted display, the original augmented reality headset, circa 1968. Augmented reality has gotten a lot more mobile in the past decade. (credit: Ivan Sutherland) A new report in The Information corroborates and expands upon an earlier Bloomberg report claiming that Apple is preparing to launch a high-end VR headset […]
SolarWinds patches vulnerabilities that could allow full system control
Enlarge (credit: Getty Images) SolarWinds, the previously little-known company whose network-monitoring tool Orion was a primary vector for one of the most serious breaches in US history, has pushed out fixes for three severe vulnerabilities. Martin Rakhmanov, a researcher with Trustwave SpiderLabs, said in a blog post on Wednesday that he began analyzing SolarWinds products […]
Malicious Chrome and Edge add-ons had a novel way to hide on 3 million devices
Enlarge (credit: Getty Images) In December, Ars reported that as many as 3 million people had been infected by Chrome and Edge browser extensions that stole personal data and redirected users to ad or phishing sites. Now, the researchers who discovered the scam have revealed the lengths the extension developers took to hide their nefarious […]
Hate the Apple TV remote? Use a gorgeous modded Game Boy instead
A modified Game Boy Color being used as an Apple TV remote. [credit: Otto Climan ] A tech DIY YouTuber named Otto Climan worked with Retro Modding to make a beautiful, classic Apple-style Game Boy Color with an updated screen and the ability to work as an Apple TV remote. There’s no overstating the love-it/hate-it […]
Boston Dynamics’ robot dog gets an arm attachment, self-charging capabilities
Boston Dynamics’ “Spot” robot is getting some upgrades. The robot dog officially went on sale to the public last year for a cool $74,500. For the first time in the company’s 29-year history, Boston Dynamics actually started selling robots to the general public, and it’s pretty incredible that you can actually just head to the […]
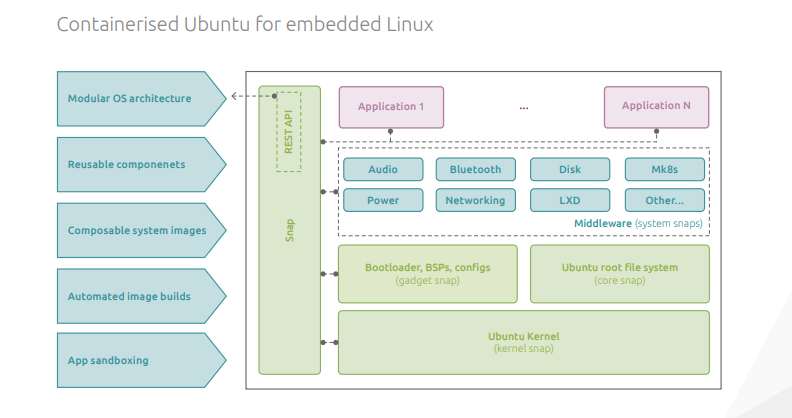
Containerize all the things with Ubuntu Core 20
Enlarge / You might draw a fairly similar schematic diagram to give someone a simplified idea of how a traditional Linux distribution is put together—but it wouldn’t be as close to literal accuracy as this Ubuntu Core diagram is. (credit: Canonical) Canonical released Ubuntu Core 20 today, and it is now available for download. If […]
High-performance computers are under siege by a newly discovered backdoor
Enlarge (credit: Getty Images) High-performance computer networks, some belonging to the world’s most prominent organizations, are under attack by a newly discovered backdoor that gives hackers the ability to remotely execute commands of their choice, researchers said on Tuesday. Kobalos, as researchers from security firm Eset have named the malware, is a backdoor that runs […]