Enlarge / Believe it or not, this fictional version of NORAD shows off the idea of the “connected battlespace” even better than the reali thing. (credit: MGM/UA) Since the earliest days of warfare, commanders of forces in the field have sought greater awareness and control of what is now commonly referred to as the “battlespace”—a […]
Tag: Biz & IT
DDoSers are abusing Microsoft RDP to make attacks more powerful
Enlarge / Hacker attacking server or database. Network security, Database secure and personal data protection (credit: Getty Images) DDoS-for-hire services are abusing the Microsoft Remote Desktop Protocol to increase the firepower of distributed denial-of-service attacks that paralyze websites and other online services, a security firm said this week. Typically abbreviated as RDP, Remote Desktop Protocol […]
This site posted every face from Parler’s Capitol Hill insurrection videos
Enlarge (credit: Getty Images | Wired) When hackers exploited a bug in Parler to download all of the right-wing social media platform’s contents last week, they were surprised to find that many of the pictures and videos contained geolocation metadata revealing exactly how many of the site’s users had taken part in the invasion of […]
Home alarm tech backdoored security cameras to spy on customers having sex
Enlarge (credit: Getty Images / Aurich Lawson) A home security technician has admitted he repeatedly broke into cameras he installed and viewed customers engaging in sex and other intimate acts. Telesforo Aviles, a 35-year-old former employee for home and small office security company ADT, said that over a five-year period, he accessed the cameras of […]
Chrome and Edge want to help with that password problem of yours
Enlarge / Please don’t do this. (credit: Getty Images) If you’re like lots of people, someone has probably nagged you to use a password manager and you still haven’t heeded the advice. Now, Chrome and Edge are coming to the rescue with beefed-up password management built directly into the browsers. Microsoft on Thursday announced a […]
Phishing scam had all the bells and whistles—except for one
Enlarge / The query window for username and password on a webpage can be seen on the monitor of a laptop. (credit: Jens Büttner/picture alliance via Getty Images) Criminals behind a recent phishing scam had assembled all the important pieces. Malware that bypassed antivirus—check. An email template that got around Microsoft Office 365 Advanced Threat […]
Ars Technicast special edition, part 1: The Internet of Things goes to war
Enlarge / This adorable robot is one data point in the connected battlespace—the web of sensors that links together all the elements in a modern engagement. (credit: Leon Neal / Getty Images) Welcome to a special edition of the Ars Technicast! Ars has partnered with Northrop Grumman to produce a two-part series looking at the […]
Security firm Malwarebytes was infected by same hackers who hit SolarWinds
Enlarge (credit: Getty Images) Security firm Malwarebytes said it was breached by the same nation-state-sponsored hackers who compromised a dozen or more US government agencies and private companies. The attackers are best known for first hacking into Austin, Texas-based SolarWinds, compromising its software-distribution system, and using it to infect the networks of customers who used […]
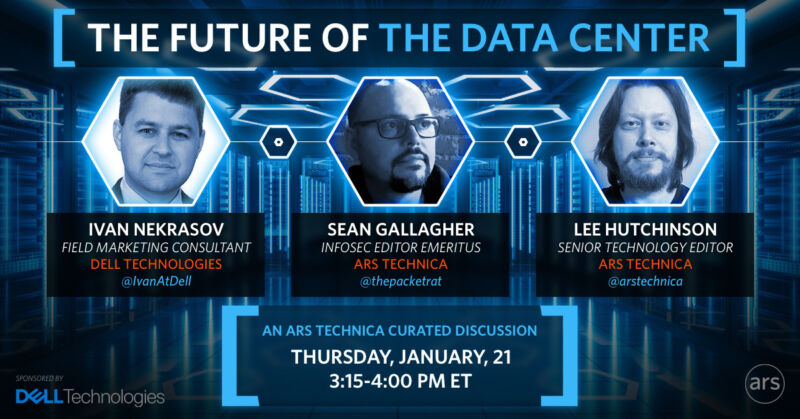
Ars online IT roundtable tomorrow: What’s the future of the data center?
Enlarge If you’re in IT, you probably remember the first time you walked into a real data center—not just a server closet, but an actual raised-floor data center, where the door wooshes open in a blast of cold air and noise and you’re confronted with rows and rows of racks, monolithic and gray, stuffed full […]
Hackers alter stolen regulatory data to sow mistrust in COVID-19 vaccine
Enlarge (credit: Getty Images) Last month, the makers of one of the most promising coronavirus vaccines reported that hackers stole confidential documents they had submitted to a European Union regulatory body. On Friday, word emerged that the hackers have falsified some of the submissions’ contents and published them on the Internet. Studies of the BNT162b2 […]