Enlarge / Mobile devices can make people vulnerable to online piracy through privacy settings, Bydgoszcz, Poland, on August 7, 2016. (Photo by Jaap Arriens/NurPhoto via Getty Images) (credit: NurPhoto | Getty Images) Apple has come under pressure to collaborate with its Silicon Valley rivals to fend off the common threat of surveillance technology after a […]
Tag: Biz & IT
Dish switching network to AT&T after calling T-Mobile anticompetitive
Enlarge (credit: Dish Network) Dish Network has agreed to pay AT&T at least $5 billion over 10 years for network access amid a feud between Dish and T-Mobile. Dish is in the early stages of building a 5G network and in the meantime is serving customers as a reseller using network capacity that it purchases […]
“Clickless” exploits from Israeli firm hacked activists’ fully updated iPhones
Enlarge (credit: Getty Images) Smartphones belonging to more than three dozen journalists, human rights activists, and business executives have been infected with powerful spyware that an Israeli firm sells, purportedly to catch terrorists and criminals, The Washington Post and other publications reported. The handsets were infected with Pegasus, full-featured spyware developed by NSO Group. The […]
US warns China over state-sponsored hacking, citing mass attacks on Exchange
Enlarge (credit: Getty Images | cbarnesphotography) The US government blamed the Chinese government on Monday for attacks on thousands of Microsoft Exchange servers. China’s Ministry of State Security (MSS) “has fostered an ecosystem of criminal contract hackers who carry out both state-sponsored activities and cybercrime for their own financial gain, ” US Secretary of State […]
Hackers got past Windows Hello by tricking a webcam
Clearly the quickest way to bypass Microsoft facial recognition, no? Biometric authentication is a key piece of the tech industry’s plans to make the world password-less . But a new method for duping Microsoft’s Windows Hello facial-recognition system shows that a little hardware fiddling can trick the system into unlocking when it shouldn’t. Services like […]
Facebook catches Iranian spies catfishing US military targets
Enlarge (credit: Getty Images) If you’re a member of the US military who’s gotten friendly Facebook messages from private-sector recruiters for months on end, suggesting a lucrative future in the aerospace or defense contractor industry, Facebook may have some bad news. On Thursday, the social media giant revealed that it has tracked and at least […]
Disable the Windows print spooler to prevent hacks, Microsoft tells customers
Enlarge (credit: Getty Images) Microsoft hit yet another snag in its efforts to lock down the Windows print spooler, as the software maker warned customers on Thursday to disable the service to contain a new vulnerability that helps attackers execute malicious code on fully patched machines. The vulnerability is the third printer-related flaw in Windows […]
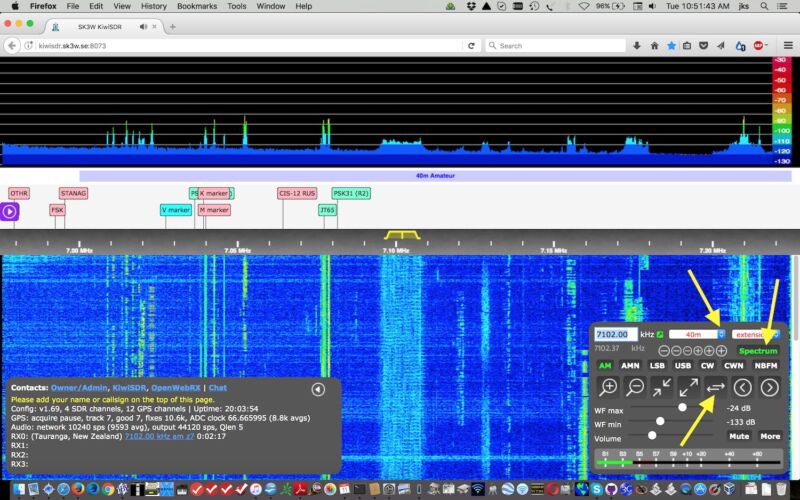
For years, a backdoor in popular KiwiSDR product gave root to project developer
Enlarge (credit: KiwiSDR) A spectrum painted image made using KiwiSDR. (credit: xssfox) KiwiSDR is hardware that uses a software-defined radio to monitor transmissions in a local area and stream them over the Internet. A largely hobbyist base of users do all kinds of cool things with the playing-card-sized devices. A user in, say, Manhattan can […]
TSMC signals global chip crunch may be easing
Enlarge / TSMC’s headquarters, seen here, are in Hsinchu, Taiwan. (credit: Sam Yeh via Getty Images ) Carmakers can expect a sharp upturn in chip supplies in the coming weeks, Taiwan Semiconductor Manufacturing Company (TSMC) said, signaling that a global shortage may have moved past its most crippling stage. In the first six months of […]
Feeding the machine: We give an AI some headlines and see what it does
Enlarge / Turning the lens on ourselves, as it were. There’s a moment in any foray into new technological territory that you realize you may have embarked on a Sisyphean task. Staring at the multitude of options available to take on the project, you research your options, read the documentation, and start to work—only to […]