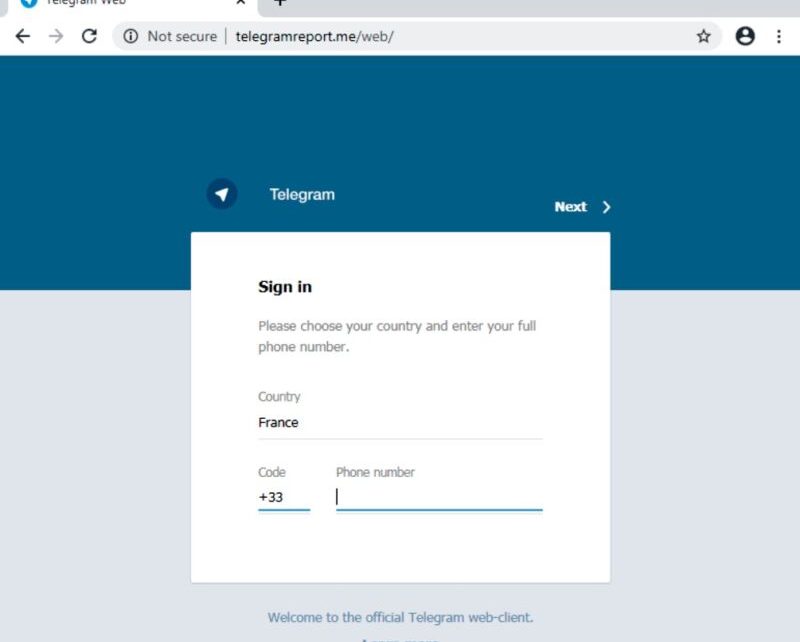
Expand / Rampant Kitty was targeting Telegram just like a feline into twine. (charge: Assess Point)
Researchers said they have found a continuing surveillance effort that for decades has been inventing a vast array of information on Windows and also Android apparatus utilized by Iranian expatriates and dissidents.
The effort, which security company Check Point has called Rampant Kitten, contains two major elements, one for Windows and another for Android. Rampant Kitten’s goal will be to steal Telegram contacts, messages, along with two-factor authentication codes delivered by SMS and after that {} take screenshots and record noises in earshot of an infected phone, the investigators stated in a article printed on Friday.
The Windows infostealer is installed via a Microsoft Office file using a name that roughly translates into”The Regime Fears the Spread of their Revolutionary Cannons.docx.” Once opened, it urges visitors to allow macros. When a person succeeds, a malicious macro downloads and installs malware. The Android infostealer is set up via a program that masquerades as a support to assist Persian-language speakers in Sweden receive their driver’s permit.